In 2025, cybercrime has become one of the most serious threats to businesses in Poland and Europe. With the entry into force of the amendment to the Act on the National Cybersecurity System (implementing the NIS2 directive), companies' responsibility for protecting data, IT systems, and responding to incidents is growing. From a criminal law perspective, a cyberattack is not only a technical threat but also a potential computer crime – and its consequences can include financial, reputational, and criminal sanctions.
In this article, we explain how criminal law defines computer crimes, what new obligations entrepreneurs have, and how to build an effective compliance system in the area of cybersecurity.
What are computer crimes under Polish law?
For over a decade, Polish criminal law has provided for a number of provisions penalizing so-called computer crimes ( cybercrimes ).
The most important of them are:
- Art. 267 of the Penal Code – unlawful obtaining of information (e.g. hacking into an IT system, breaching security);
- Art. 268a of the Penal Code – disruption of the operation of a computer system or IT network;
- Art. 269–269b of the Penal Code – attacks that threaten public security or critical infrastructure;
- Art. 287 of the Penal Code – computer fraud (e.g. manipulation of data in the system in order to obtain financial benefits).
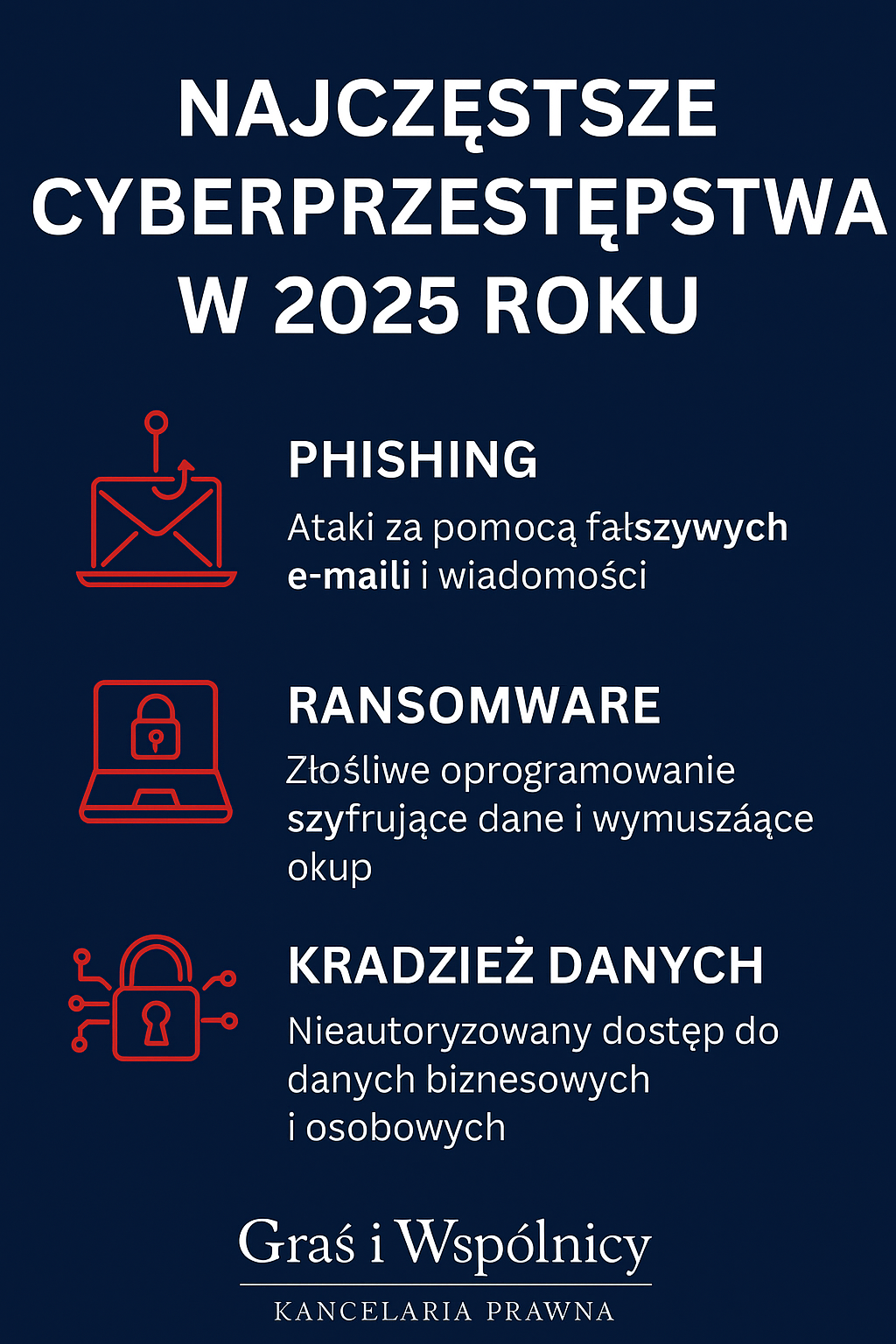
In practice, these crimes include phishing, ransomware, DDoS attacks, personal data theft, and manipulation of financial systems. Their consequences include not only financial losses but also legal liability for violations of data protection regulations (GDPR) and national cybersecurity regulations.
According to the CERT Polska report for 2024, the number of reported incidents increased by over 30% year-on-year, with the largest share of ransomware and phishing attacks on companies in the financial and professional services sectors.
What cybersecurity responsibilities do companies have in 2025?
The amendment to the National Cybersecurity System Act (NCS), implementing the NIS2 directive, will take effect in 2025 and expands the scope of entities covered by the obligations.
This applies to companies in the following sectors, among others:
- digital services,
- finance,
- transport,
- health care,
- energy,
- IT infrastructure providers.
Key responsibilities of businesses:
- Implementation of a risk management system in the IT and OT area.
- Reporting security incidents to CSIRT NASK or CERT Polska within 24 hours.
- Documenting incident response procedures.
- Employee training in cyber hygiene.
- Verification of suppliers and subcontractors in terms of information security.
Violation of these obligations may result in administrative sanctions of up to PLN 10 million or 2% of annual turnover (depending on the type of entity).
Criminal and organizational liability of enterprises
Although criminal liability generally rests with individuals, including management board members and system administrators, companies may also be held liable under the Act on the Liability of Collective Entities.
A company may be liable if:
- a crime was committed in connection with the company's activities,
- the incident was the result of inadequate supervision, lack of procedures or training,
- the company did not implement an effective compliance or incident response system.
The court may then order, among other things:
- a fine of up to PLN 10 million,
- ban on conducting business activity,
- forfeiture of proceeds of crime,
- publication of the judgment (which often has more serious reputational consequences than the financial penalty itself).
How to effectively implement a cybersecurity compliance program?
A cybersecurity compliance program is not just an IT security policy, but a comprehensive system of procedures, audits, and internal control mechanisms. Here are practical steps worth implementing in every organization:
1. Define responsibility and oversight
Appoint an Information Security Officer (CISO) or designate someone responsible for KSC/NIS2 and GDPR compliance.
2. Develop security policies and procedures
Include:
- password and access management policies,
- classification of information,
- responding to incidents,
- communication with authorities (CSIRT, UODO, Police).
3. Phishing training and testing
Regular cyber hygiene training and social engineering testing help detect human vulnerabilities – the most common cause of incidents.
4. IT audit and penetration testing
An external audit confirms the effectiveness of security measures and provides evidence of due diligence – important in the event of criminal proceedings.
5. Integration of compliance and IT
Connect compliance procedures with IT activities – for example, through a shared incident register, risk matrix, and management reports.
Practical advice: during an inspection or legal proceedings, documenting preventive measures is crucial – even the best technical security measures will not replace formal procedures and evidence of their application.
Cyberethics and security culture – a new dimension of corporate responsibility
Modern compliance isn't just about regulations and rules—it also encompasses digital ethics and a culture of responsibility. Transparency in incident reporting, honest communication with clients, and cooperation with public authorities are now standard best practices.
Companies that respond openly to incidents minimize reputational impact and build market trust.
In 2025, organizations that treat cybersecurity as part of their ESG strategy—combining data security with ethical management and sustainability—will gain an advantage.
Summary and recommendations
Cybersecurity has become an integral part of criminal and commercial law.
By 2025, every company – regardless of industry – should:
- implement procedures in accordance with NIS2 and the KSC Act,
- conduct an IT and compliance risk audit,
- train staff in cyber hygiene and data protection,
- maintain a record of incidents and evidence of corrective actions,
- build a culture of digital ethics.
Conclusion: IT security is not just a technical issue, but a legal and ethical business obligation. Companies that ignore these obligations risk not only financial losses but also criminal sanctions and a loss of market trust.
FAQ – Frequently asked questions about cybersecurity and criminal law
1. Is a company liable for the consequences of a cyberattack if it's defrauded by phishing?
Yes – if proper security procedures or training were lacking, this could be considered negligence and result in organizational liability.
2. When should an IT incident be reported to CERT Polska?
Immediately, no later than 24 hours after its detection – in accordance with the Act on the National Cybersecurity System.
3. Does the NIS2 Directive apply to small businesses?
Not always – this applies to so-called key and important entities. However, small businesses may be indirectly covered by the obligations as subcontractors or IT service providers.
5. How to combine compliance and personal data protection with cybersecurity?
The best solution is an integrated compliance system combining GDPR, NIS2, and the Penal Code – shared registers of risks, incidents, and training.
This article is for informational purposes only and does not constitute legal advice.
Legal status as of November 12, 2025
Author:
Series editor:









